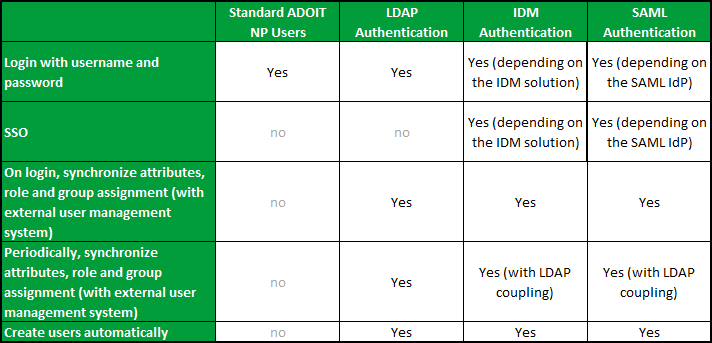
![Entity Authentication Mechanism - Enterprise-Wide Security Architecture and Solutions Presentation Guide [Book] Entity Authentication Mechanism - Enterprise-Wide Security Architecture and Solutions Presentation Guide [Book]](https://www.oreilly.com/library/view/enterprise-wide-security-architecture/0738402087/bg38.png)
Entity Authentication Mechanism - Enterprise-Wide Security Architecture and Solutions Presentation Guide [Book]

Comparison of different authentication mechanisms in cloud environment. | Download Scientific Diagram

Towards the Construction of a User Unique Authentication Mechanism on LMS Platforms through Model-Driven Engineering (MDE)

An authentication, authorization, and accounting mechanism for 3G/WLAN networks - Wu - 2016 - Security and Communication Networks - Wiley Online Library

8.2.3 Authentication and operation mechanisms of the Web GUI : JP1/Automatic Job Management System 3 Overview
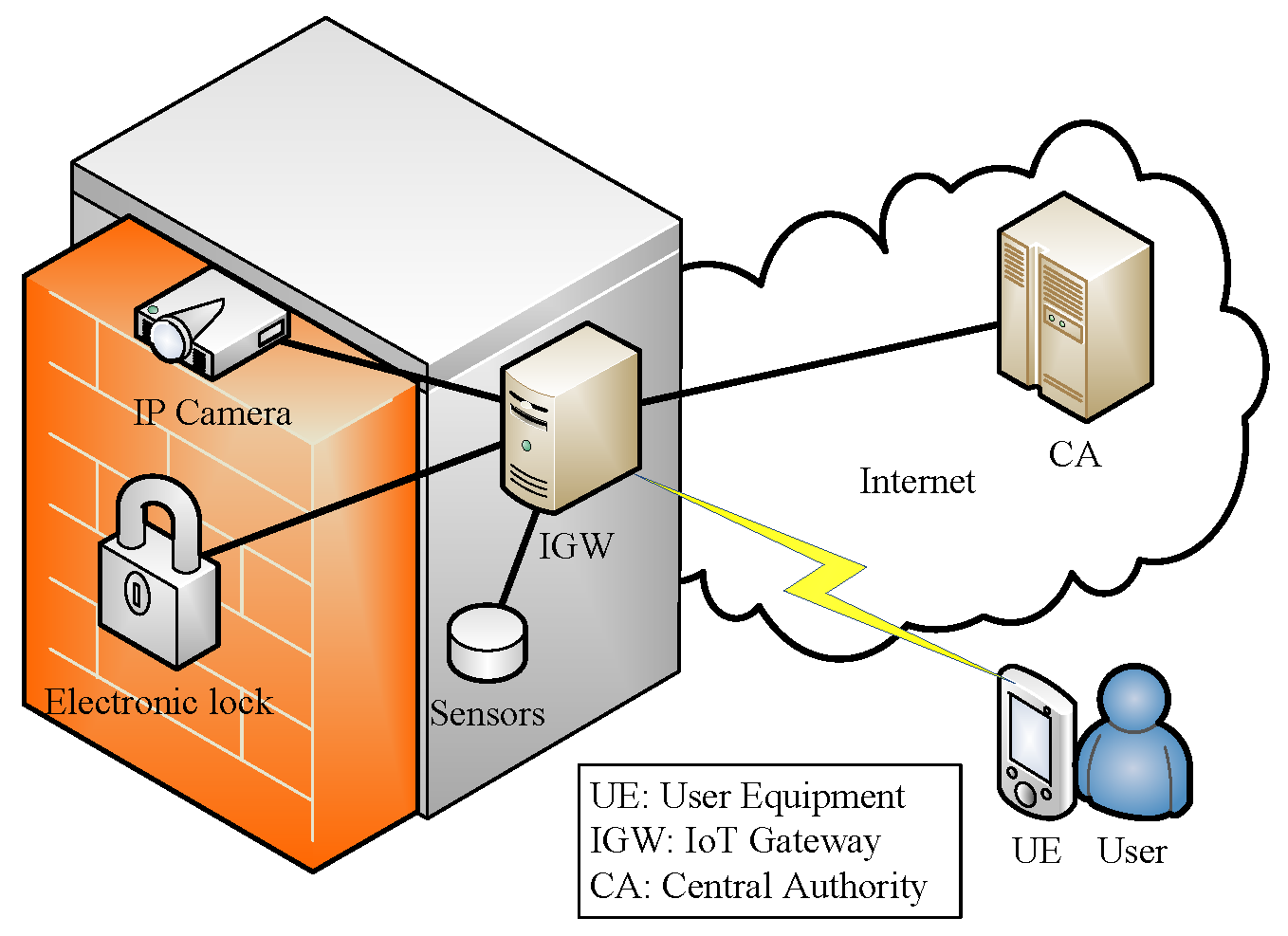
Symmetry | Free Full-Text | Geometric Authentication Mechanism for Enhancing Security in IoT Environment

Word Writing Text Email Encryption System. Business Concept for Authentication Mechanism of an Email Message Hand Drawn Stock Illustration - Illustration of guard, email: 137153212