433mhz Garage Door Remote Control Universal Car Gate Cloning Rolling Code Remote Duplicator Opener - buy from 5$ on Joom e-commerce platform

Smart access control elevator card encryption ICID copy machine Rolling code copykey copy Qi X5 universal key cutting machine
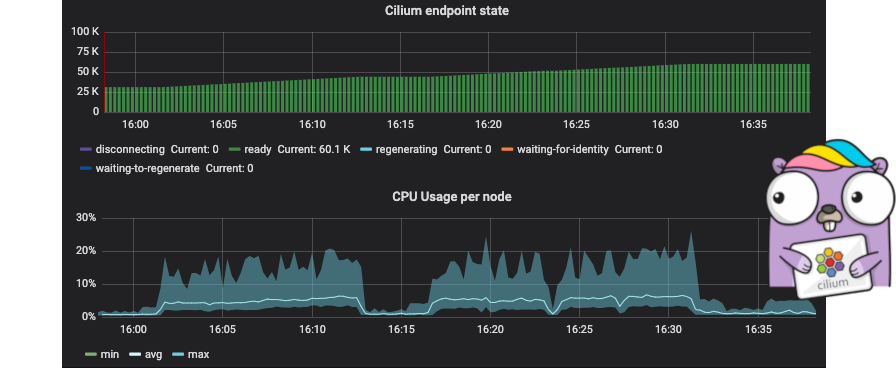
Cilium on Twitter: "Cilium 1.5 is available: * Scalability to 5k nodes, 100k pods, 20k services * BPF templating * Rolling key updates and direct-routing support for transparent encryption * BPF-based masquerading